Explore
- Active directory (4)
- AlienVault (1)
- Android (1)
- apache (1)
- ASP.net (1)
- AWS (6)
- Azure (1)
- bcpdrp (1)
- Beats (1)
- boto3 (1)
- business continuity (1)
- C# (1)
- CCISO (2)
- CCSP (2)
- CISSP (1)
- Cloud (9)
- Cloud certification (1)
- Cloud security (7)
- Cordova (1)
- Curator (1)
- Cyber kids (2)
- Cyber parents (1)
- Cyber safety (3)
- Cybersecurity KPI (1)
- Data leakage (1)
- Data privacy (1)
- Docker (1)
- ec2 (1)
- Elastalert (1)
- Elasticsearch (10)
- ELK (11)
- email signature (0)
- esp8266 (2)
- GDPR (1)
- Google Finance (1)
- Graph API (1)
- greenbone (1)
- Group Policy (1)
- IIS (1)
- Information security (8)
- Intune (1)
- iot (2)
- IT metrics (2)
- itop (1)
- IT Security (1)
- LogonTracer (1)
- Log review (2)
- Logstash (3)
- McAfee (1)
- metricbeat (1)
- Mobile security (1)
- mqtt (2)
- MSP (1)
- Neo4j (1)
- network monitoring (2)
- php (2)
- php-ldap (2)
- Powershell (1)
- Python (5)
- rds (1)
- Risk assesment (3)
- RSA (1)
- Scripting (4)
- Search guard (1)
- Security incident (1)
- SIEM (6)
- SLA (1)
- Slack (1)
- snmp (1)
- Social Engineering (1)
- Sophos (1)
- Splunk (20)
- Splunk cluster (4)
- SQL Injection (1)
- SSH tunneling (1)
- SSL installation (1)
- sysvol replication (1)
- ubuntu (1)
- Virtualization (1)
- Vulnerabilities (2)
- Wazuh (1)
- Whatsapp (1)
- Windows (2)
- Work from Home (1)
10 steps to Cyber Security
The actions and steps described below are in accordance with the guidelines from CESG UK and represent a good foundation for effective information risk management…...
Endpoint Security and Endpoint Management
TANIUM CORE (Endpoint Security and Endpoint Management ) Ask Know Act The platform for manageability and security The best endpoint solution in the market today…...
Amazon IaaS (aws) it is called VPC.
What is a Virtual Private Cloud? If you host it in amazon IaaS (aws) it is called VPC. Logically isolated network Existing within a single…...
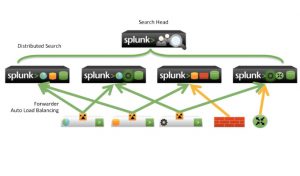
Splunk listens to your data.
Splunk listens to your data. What story are we trying to tell? What visualization that story best? What is the best way to search for…...
How to setup multi-site Search Head cluster
To deploy a multisite cluster, you configure the set of nodes for each site: A single master resides on one of the sites and controls…...