CLOUDCYBERSAFE Examples
InfoSec Solutions, Thoughts and Innovation
We talk about
Cloud Security
Data Analysis
CyberSecurity

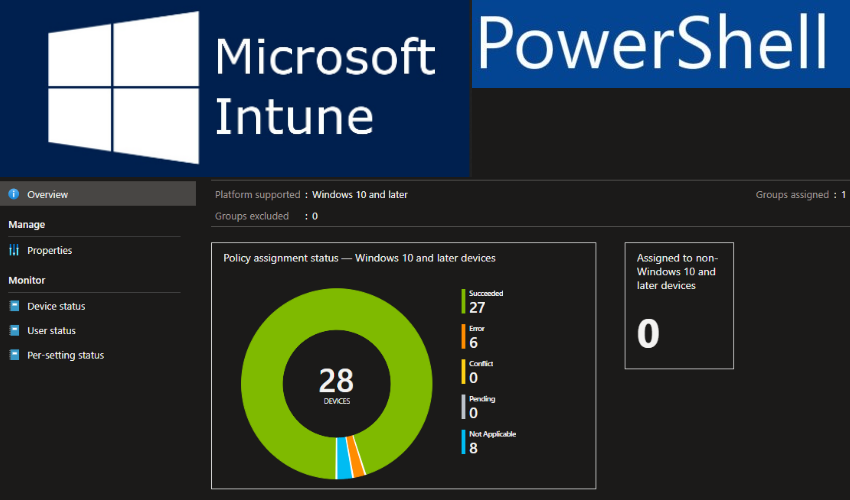
Device compliance policies are a key feature when using Intune to protect your organization's resources. In Intune, you can create
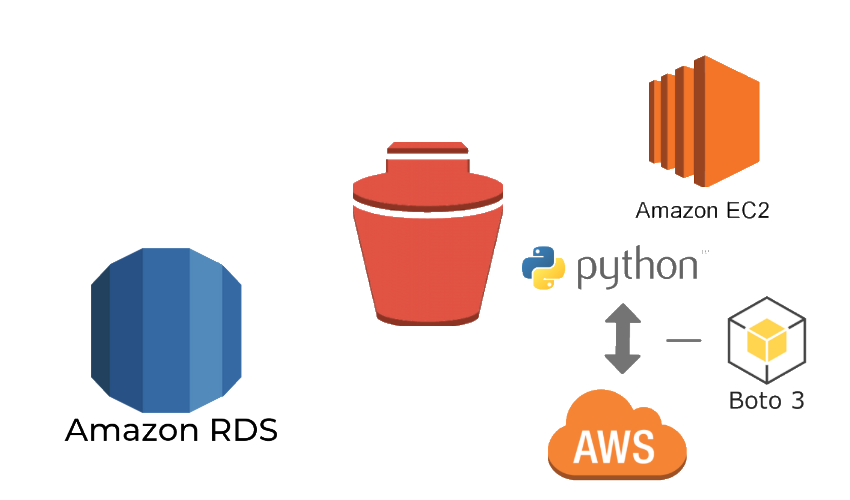
Applying filters to describe_snapshots or describe_db_snapshots functions and getting the desired results are really hard to implement. The best method
*Windows Server 2016 and 2019 Do Not Support FRS for SYSVOL Replication* The SYSVOL folder on any Active Directory domain
11 STEPS FOR ALIGNING YOUR BC/DR PROGRAM WITH BUSINESS NEEDS Disaster recovery wouldn’t be complex if organizations could adopt a
Usage of proper SIEM Use Cases is critical in setting up the security operations center (SOC) operations. A use case
Scridea’s IT Operations & Monitoring tools are designed to help IT professionals manage their tasks efficiently and easily. Manage and
Observium is an auto-discovering network monitoring tool with low-maintenance and support for Cisco, Juniper, Linux, Windows, HP, Dell, FreeBSD, Brocade,
investpy is a Python package to retrieve data from Investing.com, which provides data retrieval from up to 39952 stocks, 82221 funds,
Metricbeat is a lightweight shipper that you can install on your servers to periodically collect metrics from the operating system
MQTT is a machine-to-machine messaging protocol, designed to provide lightweight publish/subscribe communication to IOT devices. It is commonly used for
Components used : ESP8266, MQTT Server with TLS, Google Spread Sheet, Python and OLED Display Whilst planning to make a
LogonTracer associates a host name (or an IP address) and account name found in logon-related events and displays it as
Introduction Today, with advanced technology, there has been an increase in the number of cyber threats. Social engineering has become
Sophos received a report on April 22, 2020, at 20:29 UTC regarding an XG Firewall with a suspicious field value
ELK Stack processes events from a device via SNMP traps sent by the device. Configuring SNMP Server to send Threat
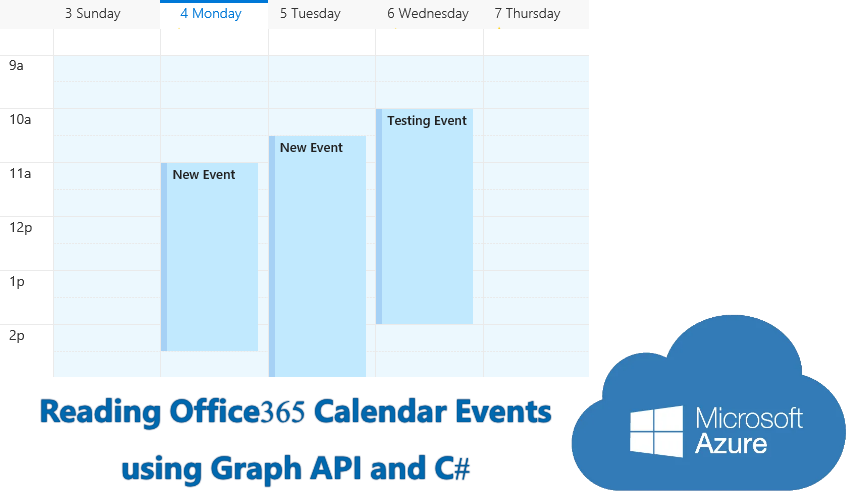
Outlook calendar is part of the Outlook messaging hub in Office 365 that also lets you manage emails and contacts,
Using Google Spreadsheets and GoogleFinance() function for Currency Meter Desktop Gadget This method show the steps to follow to use
Stay Healthy, Stay Secure : Work From Home Cybersecurity Tips Depending where in the world you live, you are either
Setting up a Zero Cost Threat Hunting Platform with Elastic Stack and Alienvault Reputation List Elastic Stack is an awesome
Configure Apache With TLS/SSL Certificate on Ubuntu Server Generate Certificate Create a directory place to store the file $ mkdir