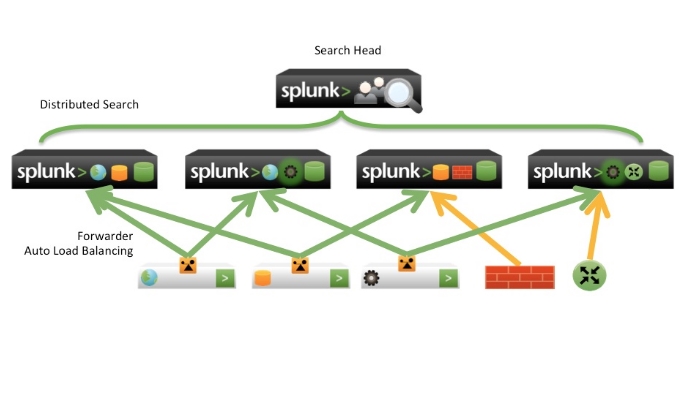
Architecting Splunk Deployment Scale Splunk Enterprise functionality to handle the data needs for enterprises of any size and complexity. Access diverse or dispersed data sources.…
IaaS Characteristics Scale Converged network and IT capacity pool Self-service and on-demand capacity High reliability and resilience IaaS key Benefits Usage is metered and price…
Deploy a multisite indexer cluster To deploy a multisite cluster, you configure the set of nodes for each site: A single master resides on one…
USB storage devices are commonly used in almost all organizations to store or transfer data. These devices act as the primary sources of malware or…
Deployment Server is for distributing configuration, and apps to Splunk Universal Forwarder, and allows you to manage remote Splunk forwarder centrally. Sending configuration file like…
Grok is a filter used by Logstash to parse unstructured data to structured format which is queryable by elasticsearch. Logstash comes with almost 120 patterns…
Private Cloud Benefits Increased control over data, underlying systems, and application Ownership and retention of governance controls. Assurance over data location, removal of multiple jurisdiction…
Knowledge of the computer hardware and physical IT infrastructure are important elements of information security. One must understand where the information physically reside on…
Implementation of LDAP-Authentication using php and OpenLDAP library which can be used for authentication of Active directory users in php forms. OpenLDAP Software is an…