Explore
- Active directory (4)
- AlienVault (1)
- Android (1)
- apache (1)
- ASP.net (1)
- AWS (6)
- Azure (1)
- bcpdrp (1)
- Beats (1)
- boto3 (1)
- business continuity (1)
- C# (1)
- CCISO (2)
- CCSP (2)
- CISSP (1)
- Cloud (9)
- Cloud certification (1)
- Cloud security (7)
- Cordova (1)
- Curator (1)
- Cyber kids (2)
- Cyber parents (1)
- Cyber safety (3)
- Cybersecurity KPI (1)
- Data leakage (1)
- Data privacy (1)
- Docker (1)
- ec2 (1)
- Elastalert (1)
- Elasticsearch (10)
- ELK (11)
- email signature (0)
- esp8266 (2)
- GDPR (1)
- Google Finance (1)
- Graph API (1)
- greenbone (1)
- Group Policy (1)
- IIS (1)
- Information security (8)
- Intune (1)
- iot (2)
- IT metrics (2)
- itop (1)
- IT Security (1)
- LogonTracer (1)
- Log review (2)
- Logstash (3)
- McAfee (1)
- metricbeat (1)
- Mobile security (1)
- mqtt (2)
- MSP (1)
- Neo4j (1)
- network monitoring (2)
- php (2)
- php-ldap (2)
- Powershell (1)
- Python (5)
- rds (1)
- Risk assesment (3)
- RSA (1)
- Scripting (4)
- Search guard (1)
- Security incident (1)
- SIEM (6)
- SLA (1)
- Slack (1)
- snmp (1)
- Social Engineering (1)
- Sophos (1)
- Splunk (20)
- Splunk cluster (4)
- SQL Injection (1)
- SSH tunneling (1)
- SSL installation (1)
- sysvol replication (1)
- ubuntu (1)
- Virtualization (1)
- Vulnerabilities (2)
- Wazuh (1)
- Whatsapp (1)
- Windows (2)
- Work from Home (1)
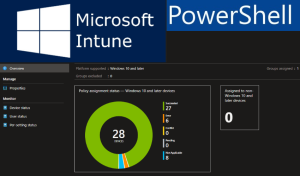
Intune Custom Compliance Policy
Device compliance policies are a key feature when using Intune to protect your organization’s resources. In Intune, you can create rules and settings that devices…...
AWS EC2 and RDS daily snapshots status using BOTO3 Python Library
Applying filters to describe_snapshots or describe_db_snapshots functions and getting the desired results are really hard to implement. The best method for fetching snapshot status is…...
Migrating SYSVOL AD Replication from FRS to DFS in Windows Server 2016 and 2019
*Windows Server 2016 and 2019 Do Not Support FRS for SYSVOL Replication* The SYSVOL folder on any Active Directory domain controller stores Group Policies settings…...
11 Steps For Aligning Your BC/DR Program With Business Needs
11 STEPS FOR ALIGNING YOUR BC/DR PROGRAM WITH BUSINESS NEEDS Disaster recovery wouldn’t be complex if organizations could adopt a “one size fits all” approach…...
SIEM Use Cases
Usage of proper SIEM Use Cases is critical in setting up the security operations center (SOC) operations. A use case can consist of multiple technical…...