SQL injection vulnerability and malicious code execution in XG Firewall/SFOS
Sophos received a report on April 22, 2020, at 20:29 UTC regarding an XG Firewall with a suspicious field value visible in the management interface. Sophos commenced an investigation and the incident was determined to be an attack against physical and virtual XG Firewall units. The attack affected systems configured with either the administration (HTTPS service) or the User Portal exposed on the WAN zone.
The attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices. It was designed to download payloads intended to exfiltrate XG Firewall-resident data. The data for any specific firewall depends upon the specific configuration and may include usernames and hashed passwords for the local device admin(s), portal admins, and user accounts used for remote access. Passwords associated with external authentication systems such as AD or LDAP are unaffected. At this time, there is no indication that the attack accessed anything on the local networks behind any impacted XG Firewall.
Timeline of attack
All times UTC
| Day and Time | Description |
|---|---|
| 2020-04-22 16:00 | Attack begins |
| 2020-04-22 20:29 | Sophos receives report of a suspicious field value in an XG Firewall management interface |
| 2020-04-22 22:03 | Incident escalated to Sophos internal cybersecurity team |
| 2020-04-22 22:20 | Initial forensics started |
| 2020-04-22 22:44 | SophosLabs blocks suspect domains found in initial forensics |
| 2020-04-23 06:30 | Sophos researchers identify indicators of attack |
| 2020-04-23 07:52 | Analysis indicates attack affecting multiple customers – major incident process initiated |
| 2020-04-23 15:47 | Sophos notifies Community of initial mitigations |
| 2020-04-23 19:39 | Initial attack vector identified as SQL injection attack |
| 2020-04-23 21:40 | SophosLabs identifies and blocks additional domains |
| 2020-04-24 03:00 | Telemetry update issued to all XG Firewalls |
| 2020-04-24 04:20 | Sophos notifies Community of additional mitigations |
| 2020-04-24 05:00 | Sophos begins design, development, and testing of hotfix to mitigate SQL injection |
| 2020-04-25 07:00 | Sophos began pushing hotfixes to supported XG Firewalls |
| 2020-04-25 22:00 | Sophos confirms completion of hotfix rollout to XG Firewall units with auto-update (default) enabled. |
Sophos immediately began an investigation that included retrieving and analyzing the artifacts associated with the attack. After determining the components and impact of the attack, Sophos deployed a hotfix to all supported XG Firewall/SFOS versions. This hotfix eliminated the SQL injection vulnerability which prevented further exploitation, stopped the XG Firewall from accessing any attacker infrastructure, and cleaned up any remnants from the attack.
Was my XG Firewall compromised?
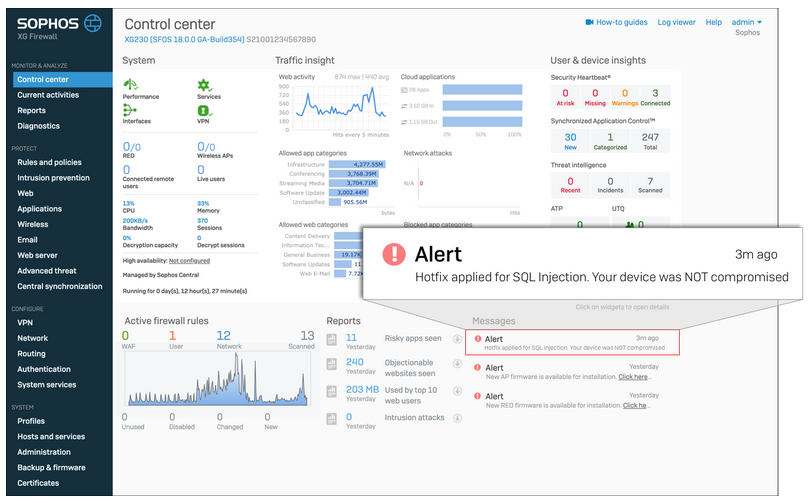
The XG Firewall hotfix that Sophos deployed includes a message on the XG management interface to indicate whether or not a given XG Firewall was affected by this attack.
Scenario 1 (Uncompromised):
Hotfix applied to an uncompromised firewall
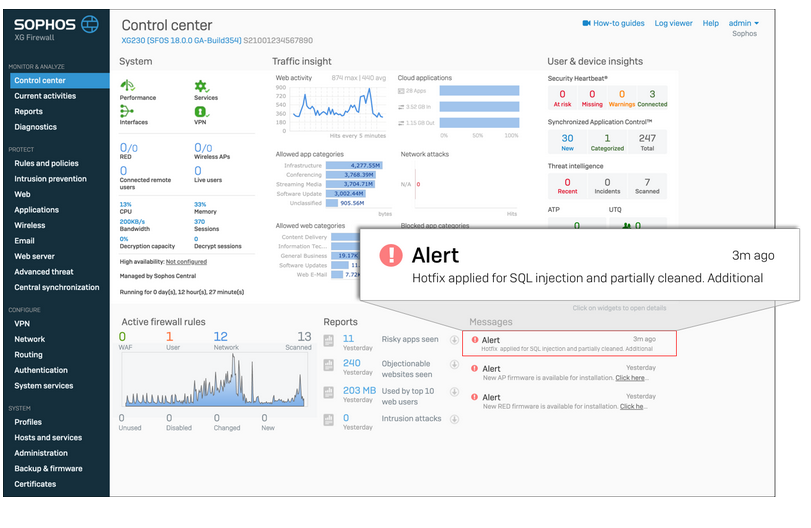
Scenario 2 (Compromised):
Hotfix applied and successfully remediated a compromised firewall
Do customers need to do anything after the hotfix is applied?
For uncompromised XG Firewall devices, no additional steps are required.
For compromised XG Firewall devices that have received the hotfix, we strongly recommend the following additional steps to fully remediate the issue:
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Note: The hotfix alert message does not disappear once the hotfix is applied. The full alert will remain visible in the XG management interface, even after the hotfix has been successfully applied and even after any additional remediation steps have been completed.
Note: While customers should always conduct their own internal investigation, at this point Sophos is not aware of any subsequent remote access attempts to impacted XG devices using the stolen credentials.