CLOUDCYBERSAFE Examples
InfoSec Solutions, Thoughts and Innovation
We talk about
Cloud Security
Data Analysis
CyberSecurity

ELK is the acronym for three open source projects: Elasticsearch, Logstash, and Kibana. Elasticsearch is a search and analytics engine
Searches are made up of this basic components Search terms - what are you looking for? -keywords, phrases, Booleans, etc.
Security flaws in the hypervisor can lead to malicious software targeting individual VMs running on it or other components in
Data in Splunk Enterprise transitions through several phases. Input Parsing Indexing Search Three key functions as it move data through
This is a simple python script that utilizes MAC to vendor API from macvendors.com to get the statistics of different devices
Risk assessment is a key component of holistic, organization-wide risk management process. Risk Management Processes include: Framing Risk Assessing risk
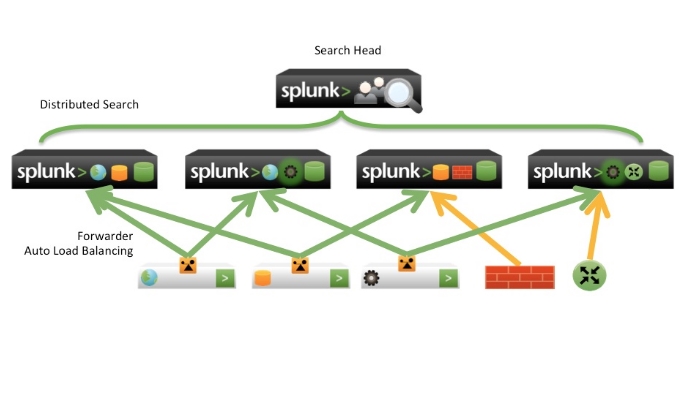
Splunk Enterprise Security should be on the search head. You will need one dedicated server to be the search head.
Many of the top risks identified in the “CLOUD SECURITY ALLIANCE the Notorious Nine: Data Breaches Data Loss Account or
Public Cloud Benefits Private Cloud Benefits Hybrid Cloud benefits Easy and inexpensive setup because hardware, application, and bandwidth costs are
When deploying a non-clustered environment, either single-server or distributed, we recommend utilizing EBS volumes and EBS-optimized instance types. An EBS
N.I.S.T Definition of Cloud Computing “Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared
For step-by-step space estimation method: Deployment Planning Total number of data sources Verify raw log sizes Daily, peak, retained, future
o Splunk Cluster Commands o $ spluk edit cluster-config -mode master –replication_factor 2 –search_factor 2 –secret ‘my_cluster_secret_key’ o $ splunk
Usage Splunk Enterprise Universal Forwareder Splunkd 8089 8089 Splunk Web http://host:8000 8000 Web app-server proxy 8065 KV Store 8191 S2S
Splunk useful commands $splunk start –accept-license $/opt/splunk/bin/splunk start --accept-license –no-prompt –answer $splunk enable boot-start –user splunker $splunk version –auth admin:changeme
Importance of metrics in an IT security program IT security metrics are widely used as the primary tools for decision