SSH Security Risks
SSH is a widely used protocol for secure remote access and file transfers over untrusted networks. A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection and it provides a way to secure the data traffic of any protocols using port forwarding techniques, simply by tunneling any TCP/IP port over SSH. The data traffic flow inside the SSH connection is encrypted so that it cannot be intercepted or eavesdropped by most deployed network monitoring and traffic filtering solutions. This obscurity carries considerable risk to an organization if it is used for malicious purposes such as data leakage or exfiltration. Most organizations restrict traffic over non standard ports and permit outgoing SSH connections for remote administration purpose of servers and appliances. This can be exploited by IT staff to log into remote machines or servers in a cloud, forwarding a port from the remote server back to their PCs or servers in their local network which enables them to use any protocols without restrictions and trace. Hackers and malware can use this for creating backdoors to the local network. The hacker sets up a remote server and once the attacker is in the target system, he connects to the outside SSH server from the inside and hide attackers’ traces.
Since the SSH connection is encrypted, SSH tunneling is also useful for transmitting data with an unencrypted protocol such as POP3,SYSLOG,VNC, RDP etc.
In this scenario the perimeter firewall is configured to block RDP connections outside the network while SSH is allowed and the RDP session could established using SSH tunneling.
To tunnel Remote Desktop Protocol over SSH, you need a user account on any appliances or machines with SSH server running, and PuTTY like SSH client on your Windows desktop.
Once the connection is established to your remote network with PuTTY reconfigure the connection to support SSH-tunneling.
In the PuTTY Reconfiguration screen, go to Connection → SSH → Tunnels. This is where we can set up an SSH tunnel for Remote Desktop.
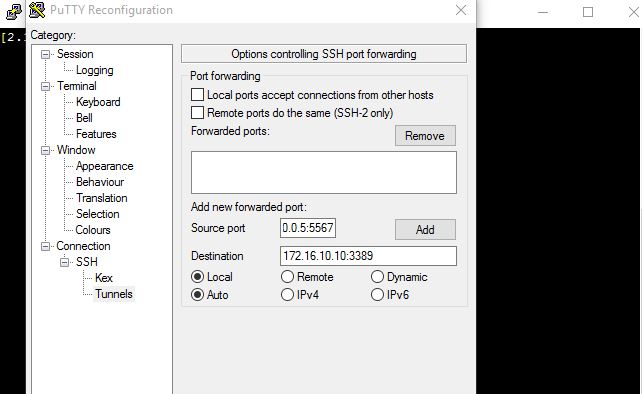
Under Source port, add your local IP address and port. Because the RDP 6+ client in Windows has issues with the loopback to TCP Port 3390, you need to use a different port. I use TCP port 5567 on IP address 127.0.0.5 which represent loopback IP, and my remote internal IP address and RDP port 3389 as Destination (172.16.10.10:3389).
On clicking Apply the SSH-tunnel for remote desktop is active, and you can connect the Remote Desktop Connection to 127.0.0.5:5567