WhatsApp Group Chat Analysis using ELK
The Elastic Stack is becoming increasingly popular with security analytics with any form of log inputs. In this post, we learn about how ELK can be used for analyze the messages in a WhatsApp group and to generate some interesting visualizations and reports. The “Email chat” feature is used to send the group chat messages to an email with media omitted and the text file containing the chat messages is downloaded from the email and copied to a filebeat installation folder. Once the file is copied the messages from the text file are pushed to the logstash beat sensor.
Logstash beat input
input {
beats {
type => "whatsapp-alerts"
port => 5012
}
}
Logstash filter excert
if [type]=="whatsapp-alerts"
{
grok{
break_on_match => false
named_captures_only => true
match => ["message" , "\s*%{NOTSPACE:logdate}\,\s*%{GREEDYDATA}\-%{SPACE}\s*%{GREEDYDATA:PhoneNumber}\:\s*%{GREEDYDATA:Message}"]
}
date {
match => [ "logdate", "ISO8601" , "M/d/yy" ]
target => "logdate"
}
mutate { add_field => { "indexType" => "WHATSAPP-LOG" }}
}
Logstash output configuration
if [indexType] == "WHATSAPP-LOG"
{
elasticsearch {
hosts => "http://localhost:9200"
index => "whatsapp-logs-%{+YYYY.MM.dd}"
document_type => doc
}
}
filebeat.yml
#=========================== Filebeat prospectors =============================
filebeat.prospectors:
# Each - is a prospector. Most options can be set at the prospector level, so
# you can use different prospectors for various configurations.
# Below are the prospector specific configurations.
- type: log
# Change to true to enable this prospector configuration.
enabled: true
# Paths that should be crawled and fetched. Glob based paths.
paths:
#- /var/log/*.log
- C:\ProgramData\filebeat-6.1.1-windows-x86_64\w\*
Text file in the specified folder

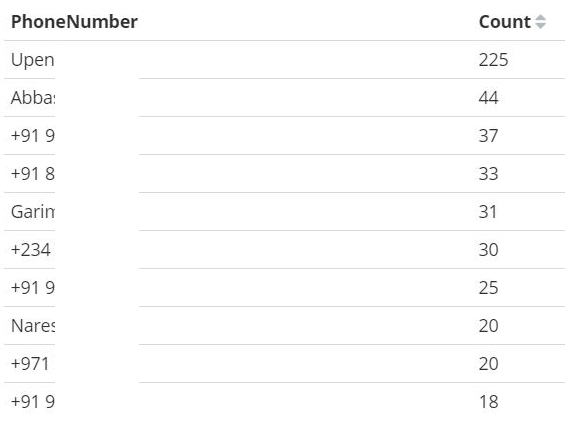
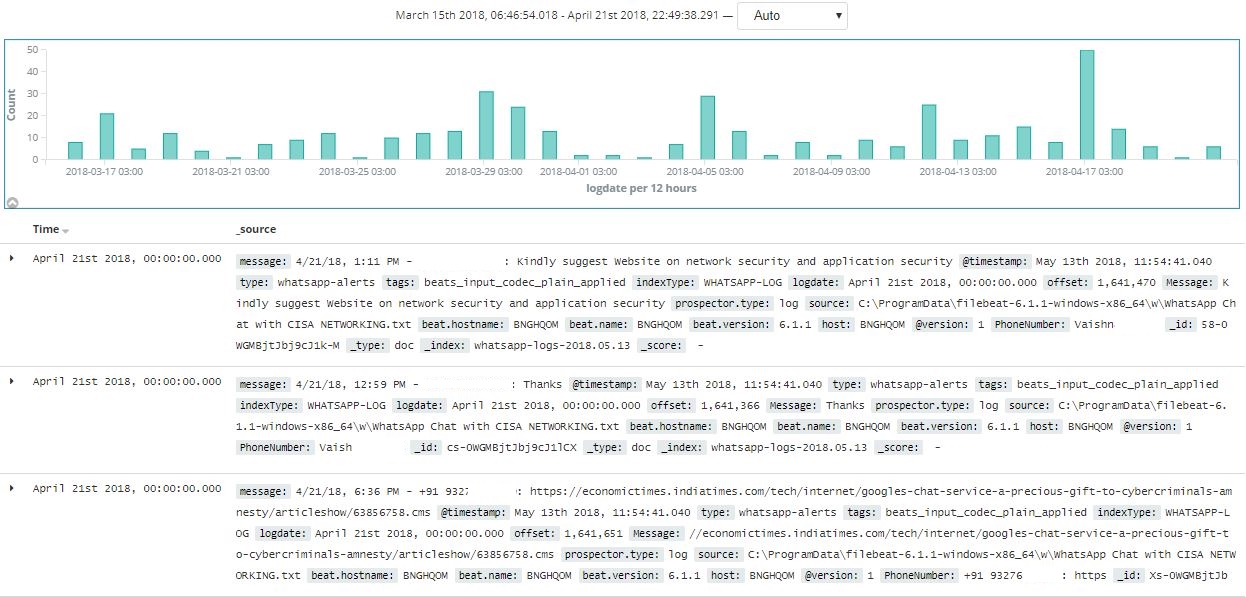
WhatsApp messages in the Kibana console
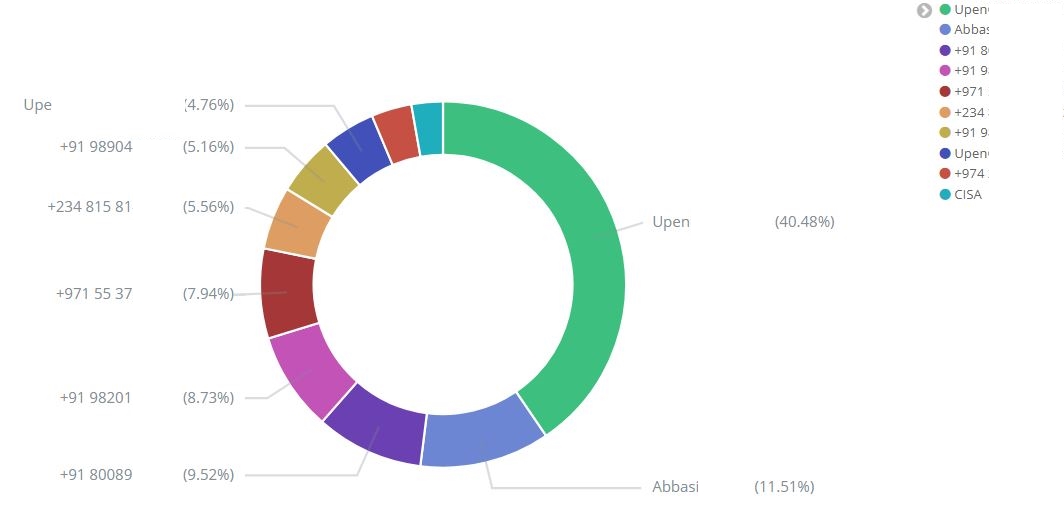
Top 10 senders during the selected time frame
Rate of messages sent to the group

Top sender’s message count